I am posting this as a follow on from this thread:
https://www.pbxforums.com/threads/s...ch-restart-cant-get-them-to-re-register.5656/
I now have great number of Yealink phones that will not connect to their provisioning server. The problem started yesterday (01/10/2021).
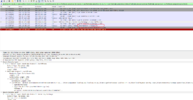
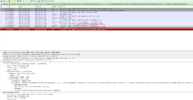
I captured the SSL exchange between the phone (a T27g) and the provisioning server, this screenshot shows the the phone rejecting the certificates saying it has expired, you can see the trust path in the Wireshark data window:
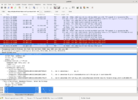
The next screen shot shows the valid dates, and it is clear that the certificate has not expired.
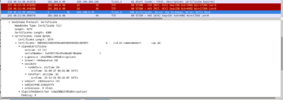
I believe the problem relates to the expiry of the DST Root CA X3 certificate. The firmware revision on the T27g mentioned above should contain the replacement ISRG Root X1.
I have raised a ticket with Yealink.
Edit: I have just seen a note attached to the Yealink trusted certificates table:
Note: ISRG Root X1, Let’s Encrypt Authority X1 and Let’s Encrypt Authority X2 certificates are only applicable to SIP-T48G/T46G/T42G/T41P/T40P/T29G/T27P/T23P/T23G/T21(P) E2/T19(P)E2 IP phones running firmware version X.80.0.95 or later.
This may explain my issues with the T27g and T46s phones.
https://www.pbxforums.com/threads/s...ch-restart-cant-get-them-to-re-register.5656/
I now have great number of Yealink phones that will not connect to their provisioning server. The problem started yesterday (01/10/2021).
I captured the SSL exchange between the phone (a T27g) and the provisioning server, this screenshot shows the the phone rejecting the certificates saying it has expired, you can see the trust path in the Wireshark data window:

The next screen shot shows the valid dates, and it is clear that the certificate has not expired.

I believe the problem relates to the expiry of the DST Root CA X3 certificate. The firmware revision on the T27g mentioned above should contain the replacement ISRG Root X1.
I have raised a ticket with Yealink.
Edit: I have just seen a note attached to the Yealink trusted certificates table:
Note: ISRG Root X1, Let’s Encrypt Authority X1 and Let’s Encrypt Authority X2 certificates are only applicable to SIP-T48G/T46G/T42G/T41P/T40P/T29G/T27P/T23P/T23G/T21(P) E2/T19(P)E2 IP phones running firmware version X.80.0.95 or later.
This may explain my issues with the T27g and T46s phones.
Last edited: