Teams Integration
- Thread starter yukon
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Mybe there is a posibility (There are also Asterisk integrations) but why dont u use kamailio and make your own SBCAnyone have any luck just using Fusion/Freeswitch as the SBC for Teams integration? I guess the first thing I should ask is, can this be done to support a multi-tenant setup for multiple 0365 domains/tenants?
I already have a Freeswitch SBC cluster fronting our PBX cluster. So I really dont want to start mucking around with Opensips or Kamailio as an additional layer if I could possibly avoid it.Mybe there is a posibility (There are also Asterisk integrations) but why dont u use kamailio and make your own SBC
I understand, i think (when you look at the asterisk or kamailio sullution) you can make a fusionpbx SBC, i made a kamailio, it just a TLS trunk to MS-TEAMS and a Contact header modify. Can you make a trunk to MS-TEAMS TLS to MS-Teams as a DR .... ?I already have a Freeswitch SBC cluster fronting our PBX cluster. So I really dont want to start mucking around with Opensips or Kamailio as an additional layer if I could possibly avoid it.
you could define a domain under SIP Settings, which will be sent on headers instead of an IP address.I understand, i think (when you look at the asterisk or kamailio sullution) you can make a fusionpbx SBC, i made a kamailio, it just a TLS trunk to MS-TEAMS and a Contact header modify. Can you make a trunk to MS-TEAMS TLS to MS-Teams as a DR .... ?
Hi Das,I use solely Freeswitch to connect FusionPBX/trunks to Teams.
I did have Kamailio too at first, then realised it is not needed. I also used Freeswitch at one time to send the options pings to MS but then found it more reliable to use SIPP for that instead.
Do you provide paid service for integrate Freeswitch or Kamailio with MS Teams?
If anyone is still having issues with that, it's because Microsoft has the requirement of at least one normalization rule per dial-plan. If you leave the rules empty, then it will apply a hidden rule that adds the +1. To stop MS from modifying the numbers in any way, just make an empty normalization rule in the dial-plan. Make a regex rule with pattern (.*) and $1 as transformation and it'll stop messing with extensions and dial rules.I now, Try Teams and Dial * look what happens.... even if you strip + in Teams dial-plan rules.
Once this is done Teams will send any number unmodified, even something like *###8.
Unless you have E5, you need the Phone System add-on, yes. You do not need any calling plans however.For those of you with teams working. What licenses did you need to get on the MS Teams side? Do you need the $12 add-on for E3?
Here's another thread talking about Teams integration: https://www.pbxforums.com/threads/ms-teams-integration.5260/
Slaver2au says "You need a device, either an appliance or virtual called an SBC. I used Anynode." Do we really need a device??
Slaver2au says "You need a device, either an appliance or virtual called an SBC. I used Anynode." Do we really need a device??
DigitalDaz, so if I understand you correctly you have an SBC in Microsoft Direct Routing that connects directly to a TLS enabled port on a Fusionpbx system. And in order to keep the Microsoft side happy you are using SipP to send regular "Options" updates to sip.pstnhub.microsoft.com:5061?
A
As of Freeswitch 1.10.3 there is a new parameter:DigitalDaz, so if I understand you correctly you have an SBC in Microsoft Direct Routing that connects directly to a TLS enabled port on a Fusionpbx system. And in order to keep the Microsoft side happy you are using SipP to send regular "Options" updates to sip.pstnhub.microsoft.com:5061?
- [mod_sofia] Add new gateway param 'contact-in-ping' to support Microsoft Teams Direct Routing
Ironic that someone on the forum would be the first to mention about the contact-in-ping parameter.
 www.pbxforums.com
www.pbxforums.com
I made a quick hack to add contact-in-ping to my gateway but I doubt that is going to work on its own??
If that is the case then it should be pretty simple to just add a gateway with the proper parameter, set up your tls certificate and be good to go. I'm betting it isn't quite that simple.
New Gateway Parameter
I am trying to make FusionPBX play well with Teams Direct Routing. A new option was added to Freeswitch release 1.10.5 named "contact-in-ping". Added new fields as "contact_in_ping" for vars and database field; and "contact-in-ping" for xml handler. Files modified...
I made a quick hack to add contact-in-ping to my gateway but I doubt that is going to work on its own??
If that is the case then it should be pretty simple to just add a gateway with the proper parameter, set up your tls certificate and be good to go. I'm betting it isn't quite that simple.
Here's the post on the freeswitch mailing list of somebody that has it working. I've also seen a few others on the maining list that have it working.
Ughh.. still not working. In all of my messing I found that the Microsoft servers communicate ONLY via tlsv1.2. My freeswitch/fusionpbx profile is running tlsv1.3 and ONLY tlsv1.3. After some digging I found that by altering my /etc/ssl/openssl.cnf file I could allow tlsv1 to run, but tlsv1.2 wouldn't work and tried to downgrade me to tlsv1.
My software stack is debian 10 (buster)
Freeswitch 1.10.7
openssl 1.1.1
Re-reading it sounds like Daz is actually running a separate instance of Freeswitch not attached to Fusionpbx to get the job done.
My software stack is debian 10 (buster)
Freeswitch 1.10.7
openssl 1.1.1
Re-reading it sounds like Daz is actually running a separate instance of Freeswitch not attached to Fusionpbx to get the job done.
So I made some progress for anyone who is interested.
In order to make tlsv1.2 work with freeswitch it was necessary to set tls-verify-depth in my sip profile to a value higher than 2 in order to make letsencrypt certificates work.
I now have calls from MSTeams -> freeswitch/fusionpbx working.
However, my calls from freeswitch/fusionpbx outbound to MSTeams gateway are still dying and being rejected by the Microsoft gateways. They are being rejected with q850 cause 42, seemingly SWITCH_CONJESTION, though I don't believe it.
My direct route gateway still show TLS connectivity status as "Inactive"
In order to make tlsv1.2 work with freeswitch it was necessary to set tls-verify-depth in my sip profile to a value higher than 2 in order to make letsencrypt certificates work.
I now have calls from MSTeams -> freeswitch/fusionpbx working.
However, my calls from freeswitch/fusionpbx outbound to MSTeams gateway are still dying and being rejected by the Microsoft gateways. They are being rejected with q850 cause 42, seemingly SWITCH_CONJESTION, though I don't believe it.
My direct route gateway still show TLS connectivity status as "Inactive"
I notice Mark just added a new parameter today contact-in-ping that is required for TEAMS integration. Have you set that?So I made some progress for anyone who is interested.
In order to make tlsv1.2 work with freeswitch it was necessary to set tls-verify-depth in my sip profile to a value higher than 2 in order to make letsencrypt certificates work.
I now have calls from MSTeams -> freeswitch/fusionpbx working.
However, my calls from freeswitch/fusionpbx outbound to MSTeams gateway are still dying and being rejected by the Microsoft gateways. They are being rejected with q850 cause 42, seemingly SWITCH_CONJESTION, though I don't believe it.
My direct route gateway still show TLS connectivity status as "Inactive"
Maybe post up everything you have done so far and i'll help with the testing as well.
Some rough steps for posterity's sake:
Microsoft Side:
Add domain and validate domain
Assign domain to at least 1 user (otherwise you can't add an sbc for that user)
Create sbc under voice->direct routing (once fusionpbx is configured and pinging properly you will need to validate that tls connectivity status and sip options status are Active)
sbc needs to have forward p-id set as well
Create voice route with dialed number pattern .* going to your sbc
Create Dial Plan Normalization rule on global dialplan that maps ^(.*)$ to $1
Use Powershell scripts:
Create NumberTranslation StripPlus https://docs.microsoft.com/en-us/powershell/module/skype/new-csteamstranslationrule?view=skype-ps
Assign number translation rule to sbc https://docs.microsoft.com/en-us/microsoftteams/direct-routing-translate-numbers
Get really really frustrated that nothing is working, so reset the Global Calling Policy
Fusionpbx Side:
Configuration:
edit /etc/freeswitch/autoload-configs/sofia.conf.xml
to enable capture server <param name="capture-server" value="udp:127.0.0.1:9060"/>
Troubleshooting without sngrep was pretty much impossible for me.
I use a simple bash script to read my encrypted sngrep now.
#!/bin/sh
fs_cli -x 'sofia global capture on'
sngrep -L udp:127.0.0.1:9060 -d lo
fs_cli -x 'sofia global capture off'
Profile:
Create a new external (or Internal could work as well depending on how you want to play it) sip profile.
set appropriate tls-sip-port and sip-port (I decided to implement a Gateway and a profile for each Microsoft tenant, this may not be necessary)
Set ext-sip-ip and sip-ip to be FQDN of Microsoft Teams direct routing SBC
Configure and set up proper tls certificate and place into tls-cert-dir parameter of new profile (The only cert necessary should be agent.pem, but I created a letsencrypt post renewal-hook that does my own thing.)
agent.pem, dtls-srtp.pem, tls.pem, and wss.pem are all symlinks to all.pem
My script looks like this:
#/bin/bash
cat /etc/letsencrypt/live/example.com/fullchain.pem /etc/letsencrypt/live/example.com/cert.pem /etc/letsencrypt/live/example.com/privkey.pem > /etc/freeswitch/ssl/example.com/all.pem;
chown www-data.www-data -R /etc/freeswitch/ssl/*
/usr/bin/fs_cli -x 'fsctl shutdown elegant restart' > /dev/null 2>&1;
sleep 5;
systemctl restart freeswitch.service; # Freeswitch sucks at restarting elegantly, and doesn't get new keys without a full restart. So, I found that I have to force a restart.
/usr/sbin/service nginx restart;
set tls-verify-depth from 2 to 9
Make sure and
Gateway:
Create three new gateways to microsoft teams sip.pstnhub.microsoft.com sip2.pstnhub.microsoft.com and sip3.pstnhub.microsoft.com
set proxy in gateway ie sip.pstnhub.microsoft.com:5061
set register transport to tls
set profile to the profile I just made
put in a hack in gateway sofia.conf.lua script to slap in contact-in-ping true for these gateways (Mark's recent commit will solve this as well, I tend to lag Mark's code several months)
comment out line in sofia.conf.lua
--table.insert(xml, [[ <param name="contact-params" value="transport=tls"/>]]);
Gateway pinging is unreliable, use SIPP to send your pings, I did this using a simple cron job, however SIPP must be downloaded and compiled with tls support as the built in packages in debian and ubuntu don't include ssl support.
ACL:
add microsoft ranges 52.112.0.0/14 and 52.120.0.0/14 to domains ACL list
reload ACL
Firewall:
create specific inbound firewall rules for new external port allowing Microsoft ranges to connect
TestTLS:
test tls connection using openssl s_client -connect sbc.example.com:yourport-tls1_2
Inbound Route:
sets the domain and routes the call to that destination inside of the domain, sets privacy (if you are getting "Private Number")
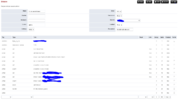
Dialplan rule:
This handles getting extension info for outbound calls
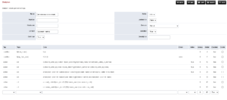
Extensions:
Create extension for each Extension you want to run in Microsoft Teams and modify the dialstring to bridge to the gateway created for teams.
Parking:
Set up a parking lot with numbers only so that Teams users can transfer to it and pick up calls out of it and so that calls can actually return to Teams extensions
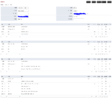
Microsoft Side:
Add domain and validate domain
Assign domain to at least 1 user (otherwise you can't add an sbc for that user)
Create sbc under voice->direct routing (once fusionpbx is configured and pinging properly you will need to validate that tls connectivity status and sip options status are Active)
sbc needs to have forward p-id set as well
Create voice route with dialed number pattern .* going to your sbc
Create Dial Plan Normalization rule on global dialplan that maps ^(.*)$ to $1
Use Powershell scripts:
Create NumberTranslation StripPlus https://docs.microsoft.com/en-us/powershell/module/skype/new-csteamstranslationrule?view=skype-ps
Assign number translation rule to sbc https://docs.microsoft.com/en-us/microsoftteams/direct-routing-translate-numbers
Get really really frustrated that nothing is working, so reset the Global Calling Policy
Fusionpbx Side:
Configuration:
edit /etc/freeswitch/autoload-configs/sofia.conf.xml
to enable capture server <param name="capture-server" value="udp:127.0.0.1:9060"/>
Troubleshooting without sngrep was pretty much impossible for me.
I use a simple bash script to read my encrypted sngrep now.
#!/bin/sh
fs_cli -x 'sofia global capture on'
sngrep -L udp:127.0.0.1:9060 -d lo
fs_cli -x 'sofia global capture off'
Profile:
Create a new external (or Internal could work as well depending on how you want to play it) sip profile.
set appropriate tls-sip-port and sip-port (I decided to implement a Gateway and a profile for each Microsoft tenant, this may not be necessary)
Set ext-sip-ip and sip-ip to be FQDN of Microsoft Teams direct routing SBC
Configure and set up proper tls certificate and place into tls-cert-dir parameter of new profile (The only cert necessary should be agent.pem, but I created a letsencrypt post renewal-hook that does my own thing.)
agent.pem, dtls-srtp.pem, tls.pem, and wss.pem are all symlinks to all.pem
My script looks like this:
#/bin/bash
cat /etc/letsencrypt/live/example.com/fullchain.pem /etc/letsencrypt/live/example.com/cert.pem /etc/letsencrypt/live/example.com/privkey.pem > /etc/freeswitch/ssl/example.com/all.pem;
chown www-data.www-data -R /etc/freeswitch/ssl/*
/usr/bin/fs_cli -x 'fsctl shutdown elegant restart' > /dev/null 2>&1;
sleep 5;
systemctl restart freeswitch.service; # Freeswitch sucks at restarting elegantly, and doesn't get new keys without a full restart. So, I found that I have to force a restart.
/usr/sbin/service nginx restart;
set tls-verify-depth from 2 to 9
Make sure and
Gateway:
Create three new gateways to microsoft teams sip.pstnhub.microsoft.com sip2.pstnhub.microsoft.com and sip3.pstnhub.microsoft.com
set proxy in gateway ie sip.pstnhub.microsoft.com:5061
set register transport to tls
set profile to the profile I just made
put in a hack in gateway sofia.conf.lua script to slap in contact-in-ping true for these gateways (Mark's recent commit will solve this as well, I tend to lag Mark's code several months)
comment out line in sofia.conf.lua
--table.insert(xml, [[ <param name="contact-params" value="transport=tls"/>]]);
Gateway pinging is unreliable, use SIPP to send your pings, I did this using a simple cron job, however SIPP must be downloaded and compiled with tls support as the built in packages in debian and ubuntu don't include ssl support.
ACL:
add microsoft ranges 52.112.0.0/14 and 52.120.0.0/14 to domains ACL list
reload ACL
Firewall:
create specific inbound firewall rules for new external port allowing Microsoft ranges to connect
TestTLS:
test tls connection using openssl s_client -connect sbc.example.com:yourport-tls1_2
Inbound Route:
sets the domain and routes the call to that destination inside of the domain, sets privacy (if you are getting "Private Number")

Dialplan rule:
This handles getting extension info for outbound calls

Extensions:
Create extension for each Extension you want to run in Microsoft Teams and modify the dialstring to bridge to the gateway created for teams.
Parking:
Set up a parking lot with numbers only so that Teams users can transfer to it and pick up calls out of it and so that calls can actually return to Teams extensions

Last edited:
- Status
- Not open for further replies.

