It's been a while since I installed a new version of Fusion, and I don't recall having to do anything when Fusion itself had a public internet IP and the endpoints were behind a NAT.
NAT isn't working. I can have 2 extensions registered sitting side by side, and one can't call the other.
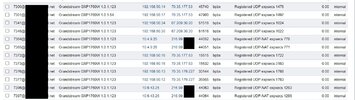
It seems I've missed something, and I've read everything I can get my hands on... On all of my production systems, when you go to the Registration page, you can see that endpoints have a status of 'Registered(UDP-NAT)(unknown)'. That's not what I see with the current version of Fusion -- What is see is 'Registered UDP' with no mention of NAT.
Ok... Just set DEBUG in the SIP profile to 1 and found this: (replaced the actual IP's first few octets with 111...)
2023-04-08 19:41:31.011432 97.20% [DEBUG] sofia_glue.c:3422 IP 111.111.111.83 is on local network, not seting NAT mode.
2023-04-08 19:41:31.311356 97.20% [DEBUG] sofia_glue.c:3422 IP 111.111.111.84 is on local network, not seting NAT mode.
The FusionPBX sits on 111.111.111.85 -- subnet is /29
The other 2 subnets have networks behind them, and SHOULD have NAT enabled.
How do I force NAT?
NAT isn't working. I can have 2 extensions registered sitting side by side, and one can't call the other.
It seems I've missed something, and I've read everything I can get my hands on... On all of my production systems, when you go to the Registration page, you can see that endpoints have a status of 'Registered(UDP-NAT)(unknown)'. That's not what I see with the current version of Fusion -- What is see is 'Registered UDP' with no mention of NAT.
Ok... Just set DEBUG in the SIP profile to 1 and found this: (replaced the actual IP's first few octets with 111...)
2023-04-08 19:41:31.011432 97.20% [DEBUG] sofia_glue.c:3422 IP 111.111.111.83 is on local network, not seting NAT mode.
2023-04-08 19:41:31.311356 97.20% [DEBUG] sofia_glue.c:3422 IP 111.111.111.84 is on local network, not seting NAT mode.
The FusionPBX sits on 111.111.111.85 -- subnet is /29
The other 2 subnets have networks behind them, and SHOULD have NAT enabled.
How do I force NAT?