I have used a wildcard cert previously with my servers and am now wanting to go back to individual to help combat TLS issues with certain devices not liking wildcards.
I haven't upgraded to 5.4 yet but will shortly, currently on 5.3
First easy question, is the https://docs.fusionpbx.com/en/latest/getting_started/lets_encrypt.html page still current to setup multiple domains up with Fusion and lets encrypt?
Do we still need to manually add the conf for every new domain added to the server or does the letsecnrypt.sh take care of that?
This is kind of un-clear as the bullet points at the top of the page imply that Nginx config is taken care of.
If I currently have my domain setup as *.mydomain.tld and is the only one I renew is there anything special that I need to do when moving to individual certs?
Here's what it seems would work:
-Run letsencrypt.sh and first just enter in my servers main host name ex. host.mydomain.tld
-Make sure it updated the path in nginx conf to the new cert path
-Then jump to here in the doc for multiple domains
-Then follow the process under "Follow the steps below every time you add a new domain" for each of the domains currently on the server -- although looking currently some of these files mentioned in the commands don't exist -- its possible that is because I have not run the commands I just want to make sure I'm not doing some old commands that are no longer relevant.
For example renew-letsencrypt.sh doesn't exist in /etc/fusionpbx and in this section: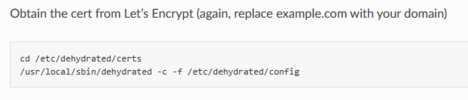
What is it trying to say, example.com isn't here.... will I be prompted? Is this editing a file? Is it referring to something else when it says "obtain the cert from let's encrypt again"
Thanks y'all
I haven't upgraded to 5.4 yet but will shortly, currently on 5.3
First easy question, is the https://docs.fusionpbx.com/en/latest/getting_started/lets_encrypt.html page still current to setup multiple domains up with Fusion and lets encrypt?
Do we still need to manually add the conf for every new domain added to the server or does the letsecnrypt.sh take care of that?
This is kind of un-clear as the bullet points at the top of the page imply that Nginx config is taken care of.
If I currently have my domain setup as *.mydomain.tld and is the only one I renew is there anything special that I need to do when moving to individual certs?
Here's what it seems would work:
-Run letsencrypt.sh and first just enter in my servers main host name ex. host.mydomain.tld
-Make sure it updated the path in nginx conf to the new cert path
-Then jump to here in the doc for multiple domains
-Then follow the process under "Follow the steps below every time you add a new domain" for each of the domains currently on the server -- although looking currently some of these files mentioned in the commands don't exist -- its possible that is because I have not run the commands I just want to make sure I'm not doing some old commands that are no longer relevant.
For example renew-letsencrypt.sh doesn't exist in /etc/fusionpbx and in this section:

What is it trying to say, example.com isn't here.... will I be prompted? Is this editing a file? Is it referring to something else when it says "obtain the cert from let's encrypt again"
Thanks y'all

